Our Mission
SoftwareBySid is built on the principle that well-engineered systems start with clean design, secure implementation, and clear documentation. My work focuses on building reliable network and infrastructure solutions with an emphasis on structured cabling, neat labeling, and scalable architecture. Security is treated as foundational—not an afterthought—guided by the CIA triad, strong identity and access management, and least-privilege design. Every deployment is documented, maintainable, and designed to reflect real-world enterprise standards.

 Installations & Deployments
Installations & Deployments
 Network Diagrams
Network Diagrams
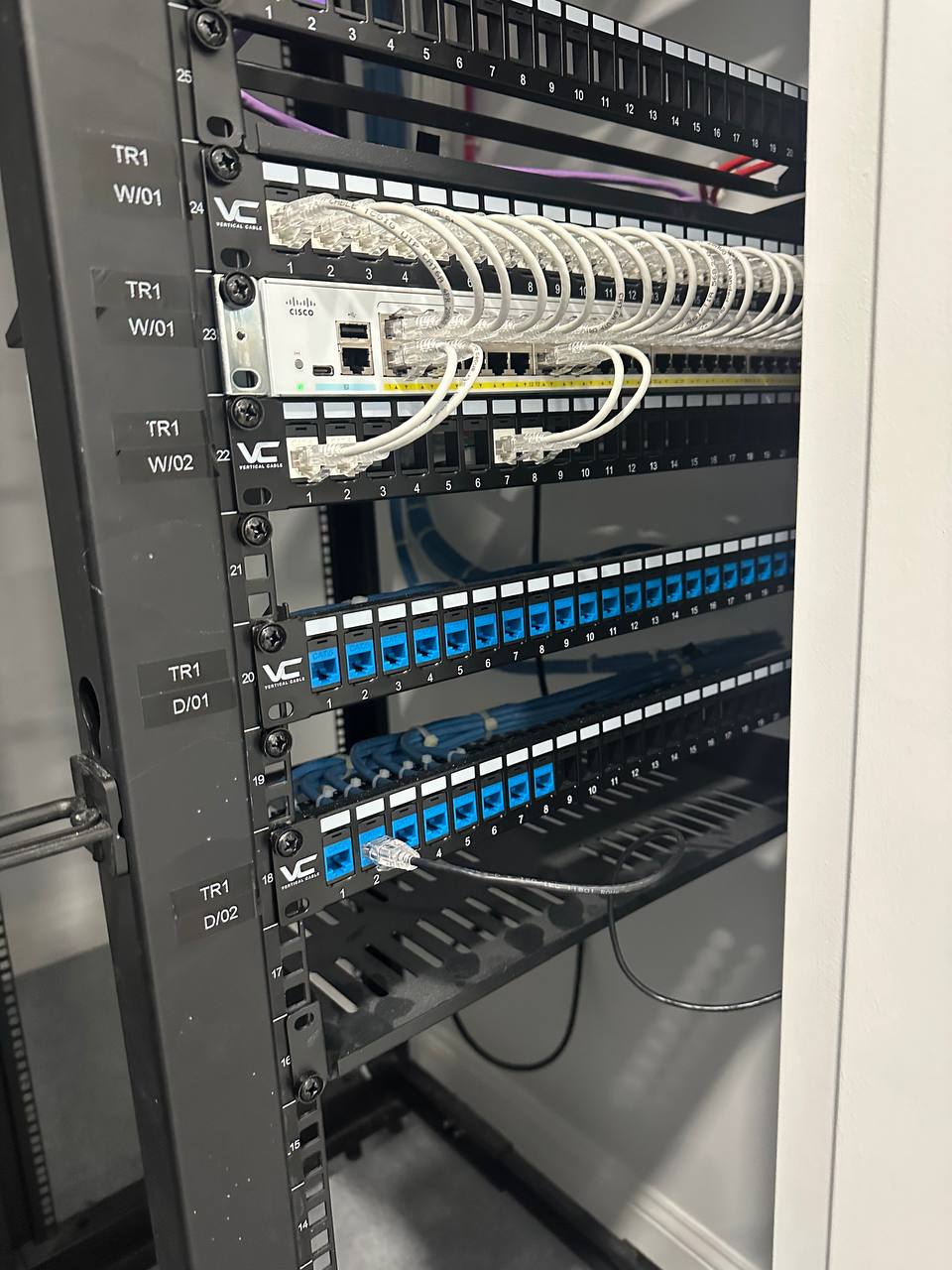
 Cable Management & Revamping
Cable Management & Revamping
 Field Installations & LV Work
Field Installations & LV Work
 Network Infrastructure Documentation
Network Infrastructure Documentation
 Certifications
Certifications
 Installations & Deployment
Installations & Deployment
 Network Design & Architecture
Network Design & Architecture
 Appliance Repair
Appliance Repair